Introducing Quay Imager
NOTE: I renamed Quay Imager to Image Hooks, links have been updated.
Short post to introduce a tiny service called “quay-imager”.
This is an HTTP server that receives Quay.io Webhook notifications and automates editing of a YAML file, by replacing an image reference.
How does this work?
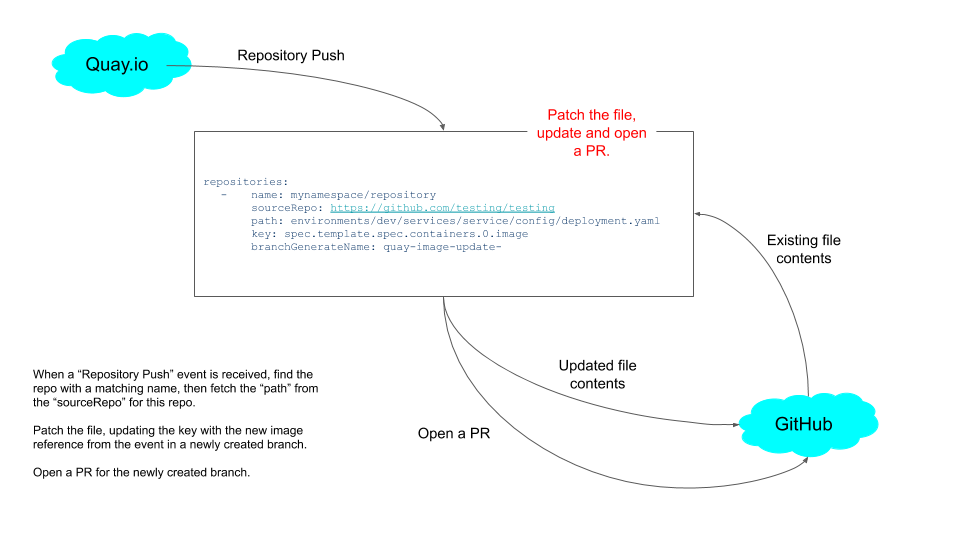
Deployment
This is packaged and deployed as a Kubernetes deployment.
Before deploying the release, you will need to do some minimal configuration.
Then deploy the release.
$ kubectl apply -f https://github.com/bigkevmcd/image-hooks/releases/download/v0.0.1/release.yaml
NOTE: There’s nothing in this code that requires to be run in a Kubernetes cluster, so you are free to build and deploy in other ways, for example Heroku.
Configuration
Given this configuration:
repositories:
- name: <Quay.io username>/<Quay.io repository>
sourceRepo: <github user>/<github repository>
sourceBranch: master
filePath: deploy/deployment.yaml
updateKey: spec.template.spec.containers.0.image
branchGenerateName: repo-imager-
This is an array of repositories, the name is used to match on the incoming
Quay.io webhooks
The sourceRepo and sourceBranch reference the file to be updated, the
filePath is the actual file to change.
The updateKey is a JSON path to update with the incoming key.
Finally, the branchGenerateName is used to generate a random branch name.
Quay.io configuration
You’ll need to expose your service so it can be accessed by Quay.io, and create a Webhook Notification for your repository.
This must be a “Push to Repository” notification, with a type of “Webhook POST”.
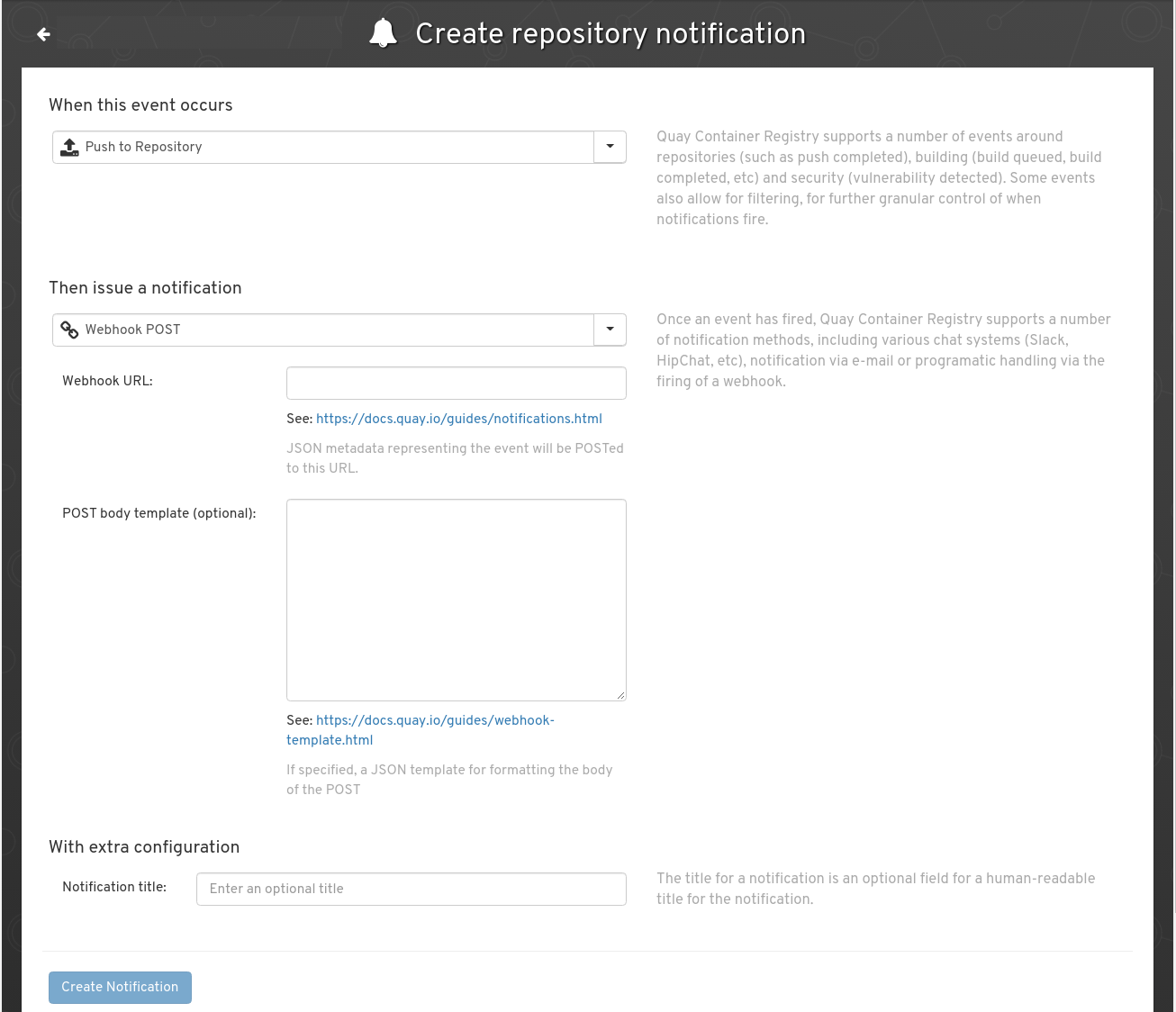
Fill in the Webhook URL with with the exposed URL (don’t forget things like ngrok if you’re testing this locally).
Finally, push an image to Quay.io:
$ docker push quay.io/<Quay.io username>/<Quay.io repository>:v1
This should trigger an update to the GitHub repository, creating a new branch (named with the prefix repo-imager-), and opening a PR with the change.
The spec.template.spec.containers.0.image field, in the deploy/deployment.yaml field is updated with the image that was pushed, for example, above, this would be replaced with something like quay.io/myuser/example:v1.
By approving this PR, ideally, you’d trigger a deployment (if you’re following GitOps processes).
IMPORTANT CAVEAT
Quay.io has no support for authenticating hooks, so unfortunately you can’t trust Webhooks, so I wouldn’t recommend this in production without some mechanism to prevent randoms on the internet triggering builds.
API
You could see this as an API for automating updating GitOps files, these are the fields you’d need to send.
It would certainly be possible to have an optional authentication header, and require API requests to send it, and block non-authenticated requests.
{
"repository": "mynamespace/repository",
"docker_url": "quay.io/mynamespace/repository",
"updated_tags": [
"latest"
]
}